How does it work
JustPass.me uses OpenID Connect (OIDC) (opens in a new tab) Standard for all the communication between your application (Web Server and/or web component).
OpenID Connect is the protocol used when a user registers/logs to a website by Facebook, Google and/or Github. It is a well established secure protocol as it is an extension to OAuth 2.0.
JustPass.me is certified to use Authorization Code Flow, Implicit Flow (token or id_token) or Hybrid Flow.
Registration Flow
As shown in the figure below, the registration flow is as follows
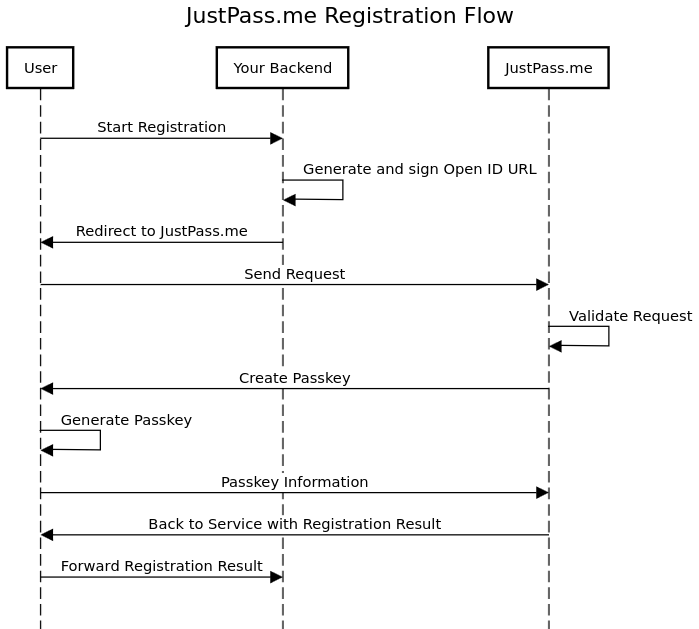
- the user clicks on
start_registration, - Your backend receives the request, generates the OIDC request and sign it.
- The user's browser redirects to received URL.
- Here the experience differs
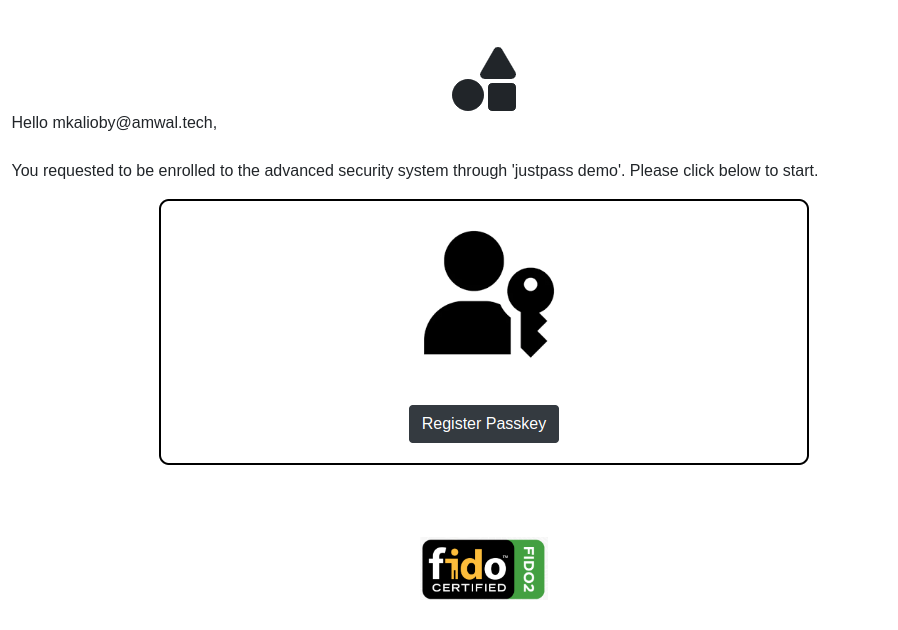
- On Website, the user see a page asking them to start registration
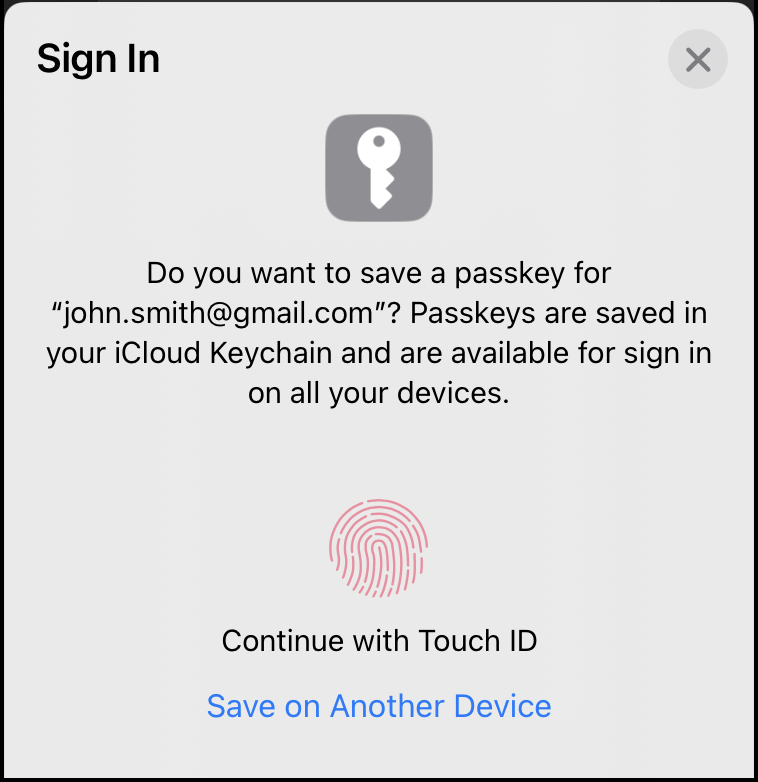
- On Mobile Applications, the user gets asked to register the passkey directly
- On Website, the user see a page asking them to start registration
- Once the keys are generated and saved on JustPass Servers, an OIDC response containing a unique code is generated and sent to the user's browser.
- The user's browser redirect back to the service with the code.
- The following steps are done automatically by OIDC Client
- Sends the authorization code to get access_token
- Sends the access_token to get id_token containing the user information
Notes:
- Your backend provides the user's identifier, which can be a username, an email or a random value which is unique to your backend.
- All registration requests are signed by your backend to make sure that your backend generated it.
Authentication Flow
JustPass.me can be used as a single factor and/or second factor system for authentication. The 2 methods are the same but it depends on what you do before calling login.
Single Factor
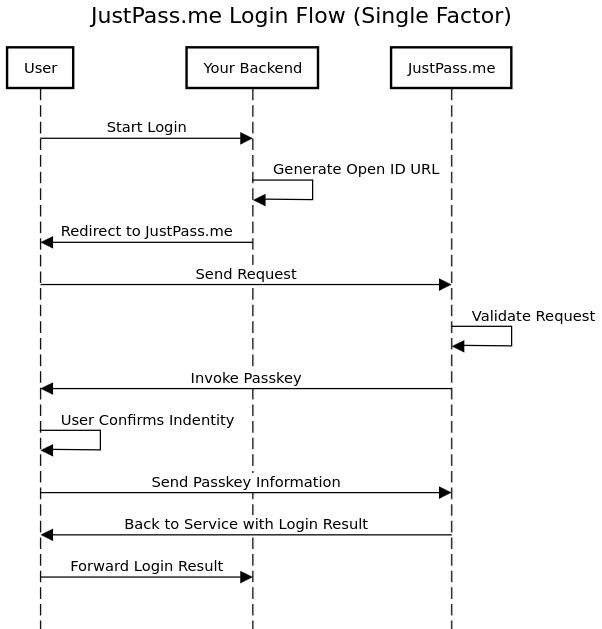
Note: Firefox doesn't support this and the user shall provide their email first.
- the user clicks on
start_login, - Your backend receives the request, generates the OIDC request.
- The user's browser redirects to received URL.
- Here the experience differs
- On Website, the user see a page asking them to Authorize
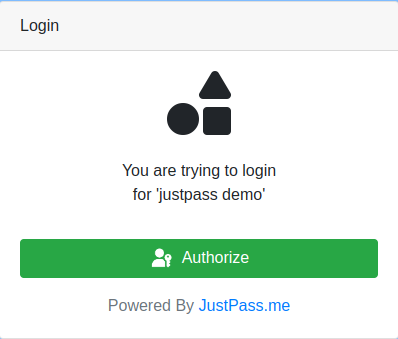
- On Mobile Applications, the user gets asked to login directly
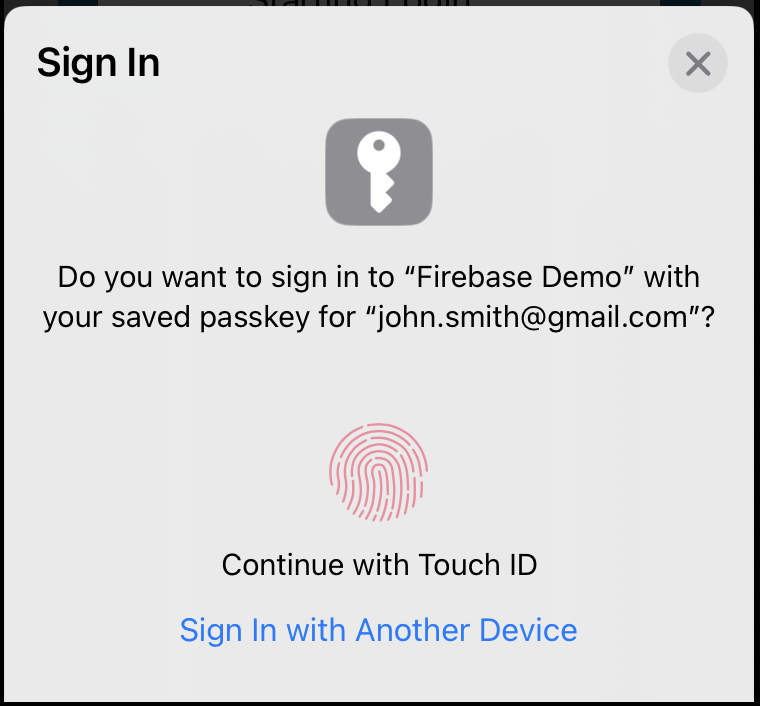
- On Website, the user see a page asking them to Authorize
- Once the user confirms their identity, an OIDC response containing a unique code is generated and sent to the user's browser.
- The user's browser redirect back to the service with the code.
- The following steps are done automatically by OIDC Client
- Sends the authorization code to get access_token
- Sends the access_token to get id_token containing the user information.
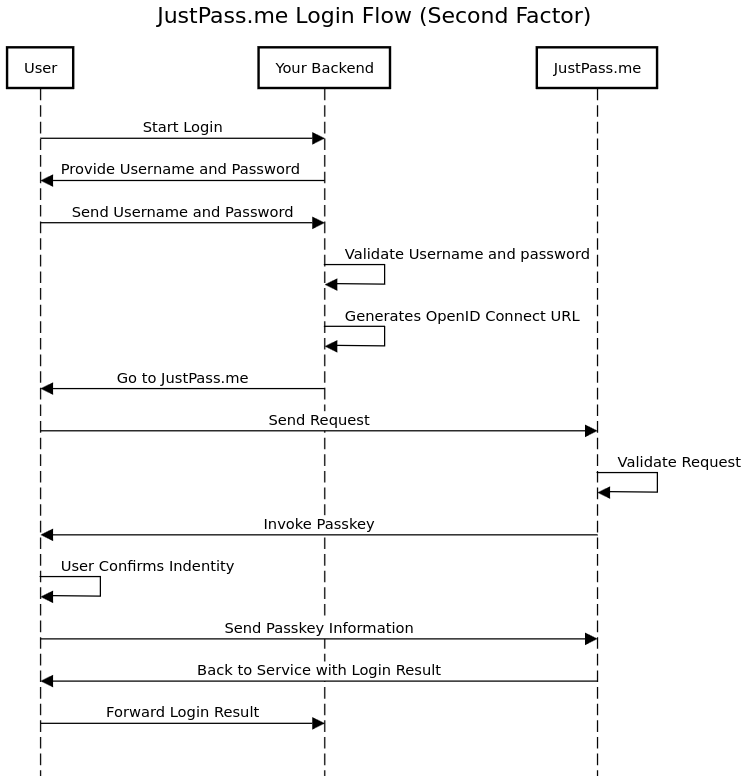
Second Factor
The main difference between the 2 flows that your backend shall validate the username and password before calling start_reg as shown below.